Beware of people using AI to create fake LinkedIn company profiles for fraud
The nature of LinkedIn’s professional environment makes it easier for people from different backgrounds and industries to communicate with one another. Threat actors have been known to use the corporate networking platform, nevertheless, for illegal purposes like spear phishing, data collection, and identity theft. Many phoney profiles that have been discovered on the website have been seen to target people from many different industries, especially those who work in government, cyber security, and education. The goal of this kind of social engineering attack is to gather personal information about a target to steal their identity or use them against them to make money.
Keenan Ramsey case
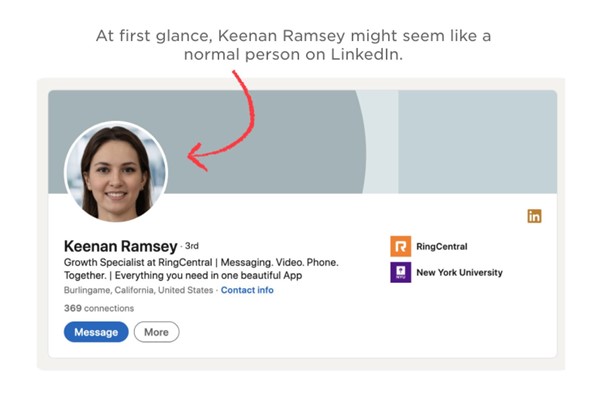
More than 1,000 LinkedIn profiles were found by the Stanford Internet Observatory’s analysis to have user accounts with profile images that were probably produced by AI. One of the researchers initiated the examination after receiving a message allegedly from “Keenan Ramsey,” whose profile image was devoid of a left earring, some hair strands, and perfectly aligned eyes.
Further research revealed no evidence of “Keenan Ramsey” working at the indicated place of employment or any documentation of her earning a degree from New York University, as claimed in her profile.
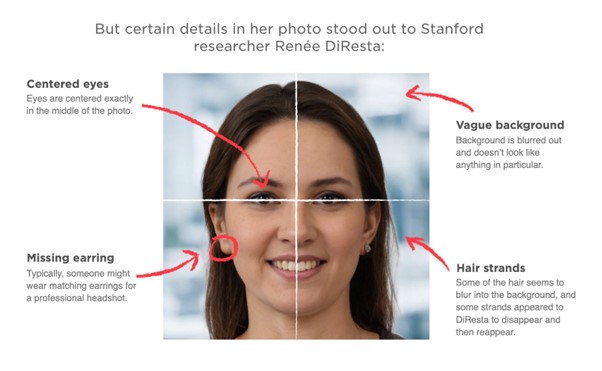
NPR, which also contacted 28 universities identified in 57 potentially fraudulent profiles found during the research, publicised the Stanford Internet Observatory findings. Twenty-one institutions of higher learning responded, stating that they had been unable to locate “any records of the putative graduates.”
Several of the artificially created accounts in this instance seemed to be utilised for digital telemarketing; automated profiles would message users, and those who responded were then forwarded to a real salesperson.
Recommended Guidelines for Interacting on LinkedIn

Connect carefully:
- Just as on other social media sites, only friend or connect with people you know in person. If you decide to communicate with an unknown person, we advise taking the next few steps:
- Examine the user’s profile image.
- Stock photos, pictures of famous persons, or digitally created headshots may be used in fake profiles.
- Google Chrome can look for an image’s origins on the internet. You may accomplish this by selecting “Search image with Google Lens” from the context menu when you right-click the relevant profile photo. The profile is probably phoney if the image may be found in numerous stock libraries and online sources.
- Keep an eye out for ambiguous or oddly phrased bios.
- Verify that employment and academic histories are accurate and consistent.
- Look for spelling mistakes, missing portions, and a lack of activity.
- Verify a profile’s number of connections.
- Do not open any links in any questionable emails you might get from LinkedIn. To check your notifications, access LinkedIn immediately on your computer or mobile device. Phishing attempts are frequently linked to fake notification emails.
- On LinkedIn, avoid making your phone number, email address, or birthday public. Limit the visibility of simply your employment history and education in your privacy settings.
- Cut off any links with unauthorised profiles. Connections still earn credibility and knowledge through a connection with you, even if your contact list is secret.
- Report suspected profiles.
Related Posts

Buy Real X Followers in India for Safe Profile Growth

Ytviews.in Threads Followers Growth Strategy Guide

How to earn money from Instagram reels in 2026
Smart Way to Manage Multi-Platform Channels and Posting

Indian IG Likes vs HQ Indian Likes: What’s the Difference



































